ServerEngine – Use REST API
Prepare Windows for API Calls #
Allow your selected port and IP trough your Windows or Linux firewall
Open Windows Defender Firewall #
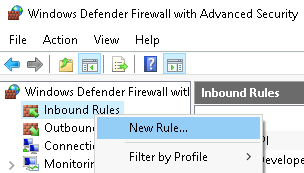
Create a new inbound rule #
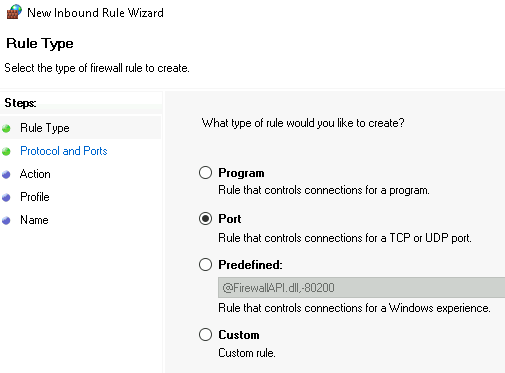
Choose type Port #
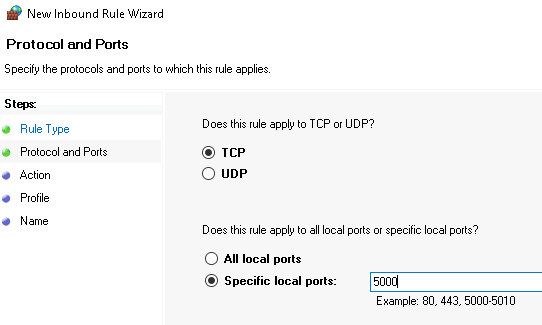
Use Protocol TCP and your configured Port #
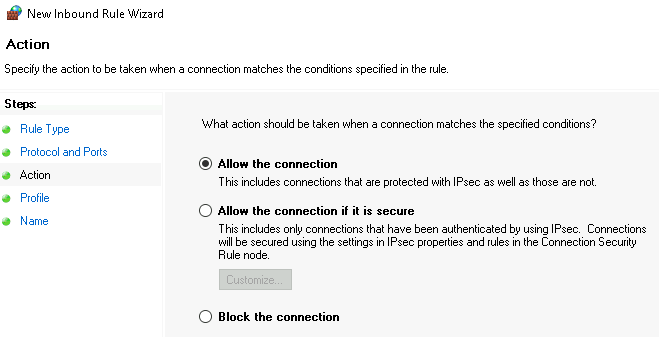
Allow the connection #
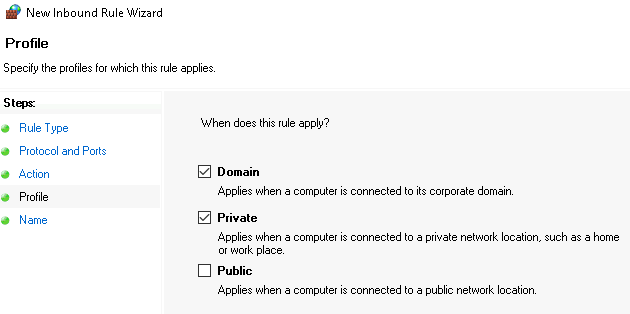
Only select Domain and Private #
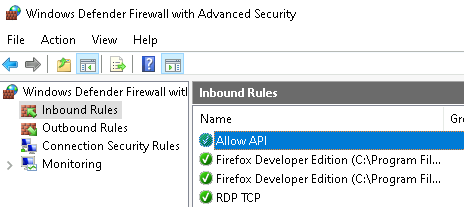
Check if rule was created #
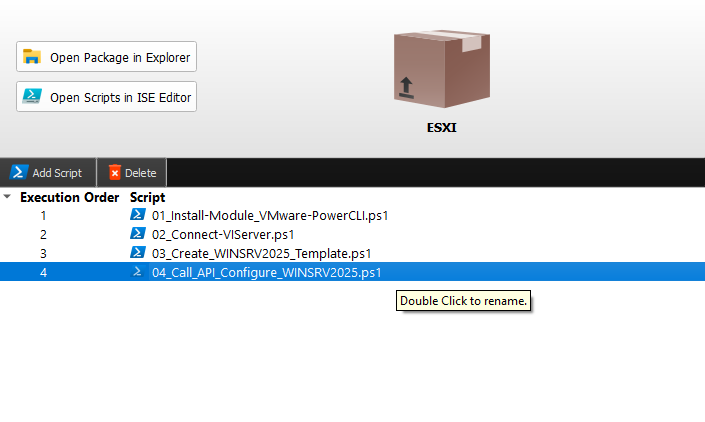
Call API from Windows #
Prepare PowerShell Script #
Replace $username and $password with your own ServerEngine credentials if changed.
$username = “admin”
$password = “cforce-it.com”
Replace with a existing PKG you want to assign to the automation.
Time = “17:28”
Date = “2024/11/04”
RepeatInterval = “Repeat: never”
Host = “AD-CA-FS.CForce-IT.network”
Package = “Showcase_Monitoring”
Status = “Enabled”
Replace “http://localhost:5000/” with your own ServerEngine IP-Address and port.
Call using PowerShell #
# Define the username and password
$username = "admin"
$password = "cforce-it.com"
# Encode the credentials
$pair = $username+":"+$password
$encodedCredentials = [Convert]::ToBase64String([Text.Encoding]::ASCII.GetBytes($pair))
# Create the headers
$headers = @{
"Content-Type" = "application/json"
"Authorization" = "Basic $encodedCredentials"
}
# Create the body
$body = @{
Time = "17:28"
Date = "2024/11/04"
RepeatInterval = "Repeat: never"
Host = "AD-CA-FS.CForce-IT.network"
Package = "Showcase_Monitoring"
Status = "Enabled"
} | ConvertTo-Json
# Make the POST request
$response = Invoke-WebRequest -Uri http://localhost:5000/ -Method POST -Headers $headers -Body $body
# Output the response content
$response.Content
Call API from Linux #
Prepare Bash Script #
Replace user -u with your own ServerEngine credentials if changed.
-u admin:cforce-it.com (username:password)
Replace “http://localhost:5000/” with your own ServerEngine IP-Address and port.
Replace with a existing PKG you want to assign to the automation.
“Time”: “12:01”,
“Date”: “2024/08/05”,
“RepeatInterval”: “Repeat: never”,
“Host”: “WIN-SRV-AUS.CForce-IT.network”,
“Package”: “Server Deployment”,
“Status”: “Enabled”
Check CURL #
CURL is usually already on most Linux Destributions if not install it with:
Ubuntu/Debian-based systems:
sudo apt install curl -y
Red Hat-based systems (RHEL/CentOS/AlmaLinux)
sudo yum install curl -y
Call using CURL #
curl -u admin:cforce-it.com -X POST http://localhost:5000/ \
-H "Content-Type: application/json" \
-d '{
"Time": "12:01",
"Date": "2024/08/05",
"RepeatInterval": "Repeat: never",
"Host": "WIN-SRV-AUS.CForce-IT.network",
"Package": "Server Deployment",
"Status": "Enabled"
}'
Incorporate API Calls into PKG #
Example: VM Deployment with ESXI and Windows Server 2025 configuration after VM creation.
# Define the username and password
$username = "admin"
$password = "cforce-it.com"
# Encode the credentials
$pair = $username+":"+$password
$encodedCredentials = [Convert]::ToBase64String([Text.Encoding]::ASCII.GetBytes($pair))
# Create the headers
$headers = @{
"Content-Type" = "application/json"
"Authorization" = "Basic $encodedCredentials"
}
# Create the body
$body = @{
Time = "18:00"
Date = "2024/12/01"
RepeatInterval = "Repeat: never"
Host = "WINSRV2025_TEMP.CForce-IT.network"
Package = "Configure_WINSRV2025"
Status = "Enabled"
} | ConvertTo-Json
# Make the POST request
$response = Invoke-WebRequest -Uri http://localhost:5000/ -Method POST -Headers $headers -Body $body
# Output the response content
$response.Content